Masters of Cybersecurity Automation Tools: Defending the Digital Future
The modern cyber battlefield is evolving rapidly, with attackers increasingly deploying AI-driven methods to exploit vulnerabilities. In this high-stakes environment, organizations are finding that human effort alone cannot keep pace. Enter cybersecurity automation tools, the new frontline of defense. By automating repetitive tasks, reducing response times, and enhancing detection accuracy, these tools are reshaping how security teams protect enterprises.
Why Cybersecurity Automation Tools Are Essential
For years, Security Operations Centers (SOCs) have struggled with alert fatigue. Analysts spend countless hours triaging false positives, manually reviewing logs, and juggling disconnected tools. This manual workload often leaves organizations slow to respond to genuine threats.
Cybersecurity automation tools like Security Information & Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) systems address these challenges head-on. They streamline processes by automating repetitive tasks, triggering incident response workflows, and providing actionable intelligence.
Just as attackers are leveraging AI to accelerate their attacks, defenders must deploy automation to match that speed. While automation is not a fully autonomous solution—human oversight remains vital—it acts as a powerful force multiplier for security teams.
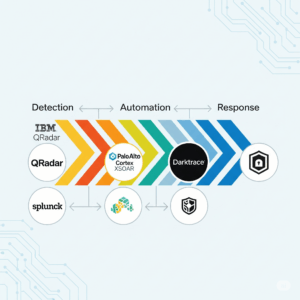
Leading Cybersecurity Automation Tools in 2025
The cybersecurity landscape is rich with automation platforms that help organizations stay ahead of attackers. Here are the most influential players:
IBM QRadar (SIEM/SOAR)
QRadar applies analytics and automated playbooks to detect and prioritize threats. By reducing manual triage, it allows analysts to focus on high-value incidents.
Palo Alto Networks Cortex XSOAR
Cortex XSOAR excels at automating workflows across multiple tools. With customizable playbooks and broad integrations, it simplifies complex incident coordination.
Splunk Phantom & Enterprise Security
Splunk provides robust analytics (Enterprise Security) and orchestration (Phantom). These tools automate case management, threat hunting, and alerting, though they come with steep complexity and licensing costs.
Tenable.io & Qualys Cloud Platform
Focused on vulnerability management, these platforms continuously scan, detect, and prioritize risks, offering remediation insights that form the backbone of proactive defense.
Ansible & Puppet (Configuration Management)
Originally DevOps tools, Ansible and Puppet enforce secure configurations, automate patching, and ensure compliance, minimizing security misconfigurations.
Darktrace & AI-Driven XDR Platforms
Harnessing self-learning AI, Darktrace identifies anomalies and autonomously contains threats. AI-driven Extended Detection and Response (XDR) systems represent the next leap in adaptive, intelligent defenses.
Challenges of Implementing Cybersecurity Automation Tools
While the benefits are clear, adopting cybersecurity automation tools is not without obstacles.
-
Integration complexity: Platforms like Cortex XSOAR and Splunk demand significant expertise and configuration, posing barriers for smaller organizations.
-
Cost factors: Advanced solutions such as QRadar or Splunk ES require not only licensing but also specialized staff, increasing total cost of ownership.
-
Trust gap: A TechRadar survey revealed that only one in ten analysts fully trust automated responses. Without transparency and explainability, automation risks being underutilized.
-
Adversary automation: Cybercriminals are adopting automation themselves, escalating the arms race where defenders must keep pace or risk falling behind.
Future Trends in Cybersecurity Automation
The evolution of cybersecurity automation tools is just beginning. Several emerging trends are shaping their future:
-
AI-Driven Incident Response: Platforms like ReliaQuest GreyMatter leverage machine learning to accelerate detection and response.
-
Automated Penetration Testing: Tools such as PenTest++ use AI to simulate attacks, uncovering vulnerabilities faster than traditional methods.
-
Standardized Protocols: Frameworks like SCAP and IEC 62443 are enabling interoperable, policy-based automation in critical infrastructure.
-
Autonomous Cyber-AI: Experimental projects, including Google Big Sleep, are exploring systems capable of independently investigating and blocking threats without human intervention—a significant leap toward preventive cyber defense.
Final Thoughts: Human Expertise + Automation
Cybersecurity automation tools are no longer optional add-ons; they are essential components of modern defense strategies. However, automation cannot replace the human element. Instead, the ideal approach is a partnership: automation handles routine and time-sensitive tasks, while human analysts provide oversight, context, and strategic judgment.
Organizations that successfully master this balance will gain a decisive edge—able to respond to evolving threats rapidly, intelligently, and with resilience. As the industry moves “behind the firewall” into this new era, it is clear: automation is not just the future of cybersecurity, it is its present.
Stay ahead in the evolving world of cybersecurity automation tools with insights from IMPAAKT, the leading top business magazine for global business and technology trends.